Enterprise Data Security
|
Design Process:
We followed a Lean UX process while designing these individual projects.
Identifying the project which is most critical first, requires minimum development effort and achieving the business goals first and starting the design.
After prioritization we started our design with Security Dashboard as first feature
We followed a Lean UX process while designing these individual projects.
Identifying the project which is most critical first, requires minimum development effort and achieving the business goals first and starting the design.
After prioritization we started our design with Security Dashboard as first feature
Research and Requirements
Qualitative research on what are different Security Events that have happened in the past with the clients, and what are the factors responsible for those events.
Quantitative research on Admin logins and their Data access pattern, How the existing users are accessing the data.
Interviews Conducted with Support teams, Customers Security admin, SMEs
Competitors Analysis on what other products are offering and what they are missing
Based on the research we come up with the list of feature to be included in the product To enhance the data security posture and to safeguard backup data from deletions triggered by rogue administrators, ransomware attacks, or operational incidents.
These features became individual projects later.
Quantitative research on Admin logins and their Data access pattern, How the existing users are accessing the data.
Interviews Conducted with Support teams, Customers Security admin, SMEs
Competitors Analysis on what other products are offering and what they are missing
Based on the research we come up with the list of feature to be included in the product To enhance the data security posture and to safeguard backup data from deletions triggered by rogue administrators, ransomware attacks, or operational incidents.
These features became individual projects later.
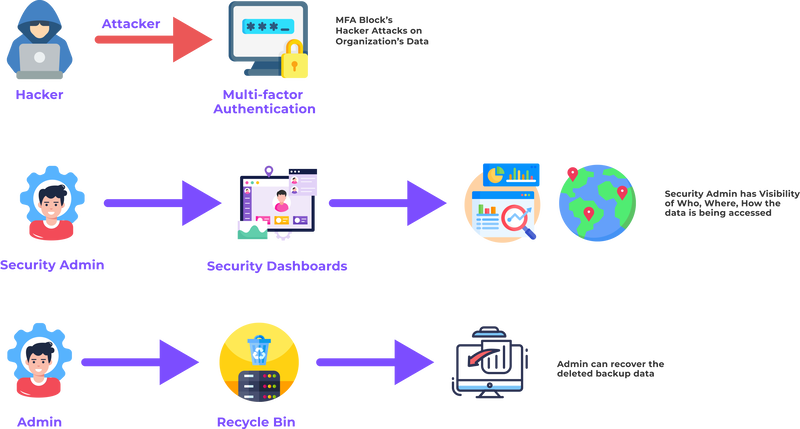
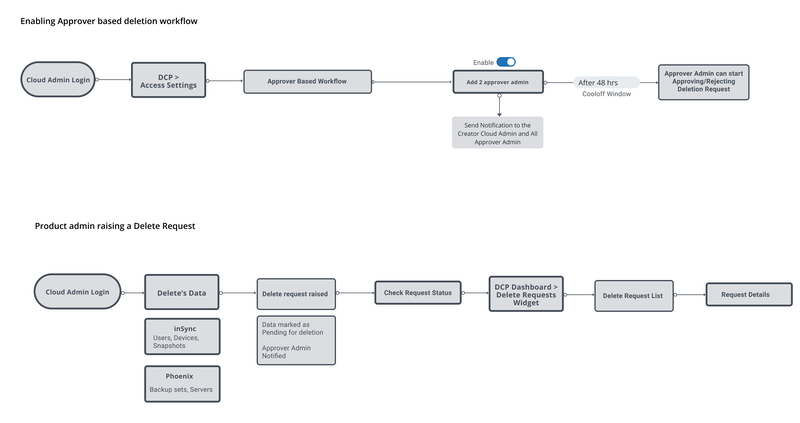
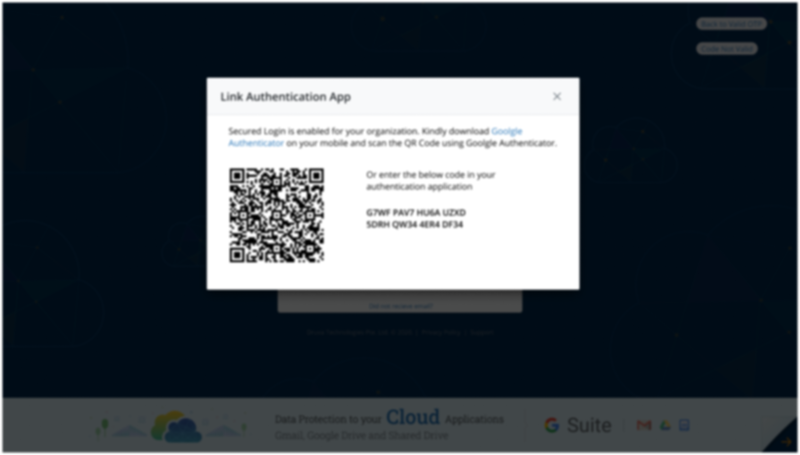
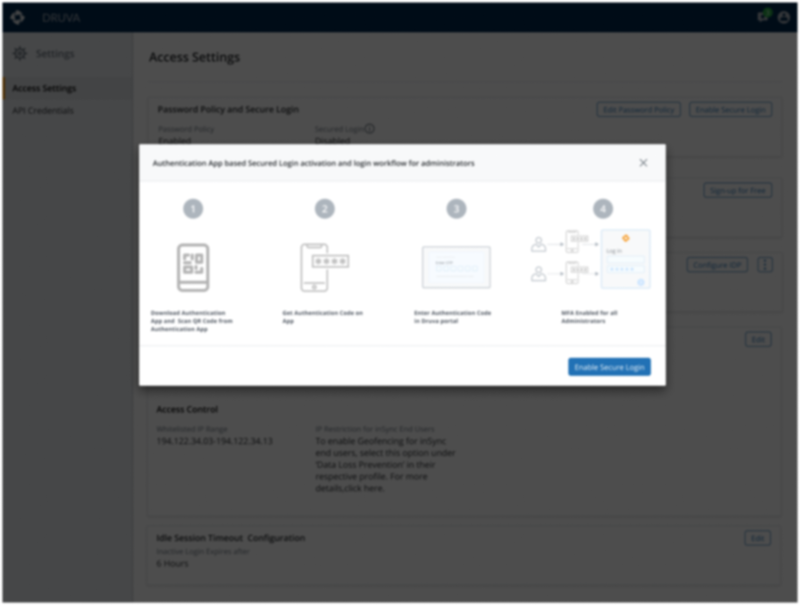
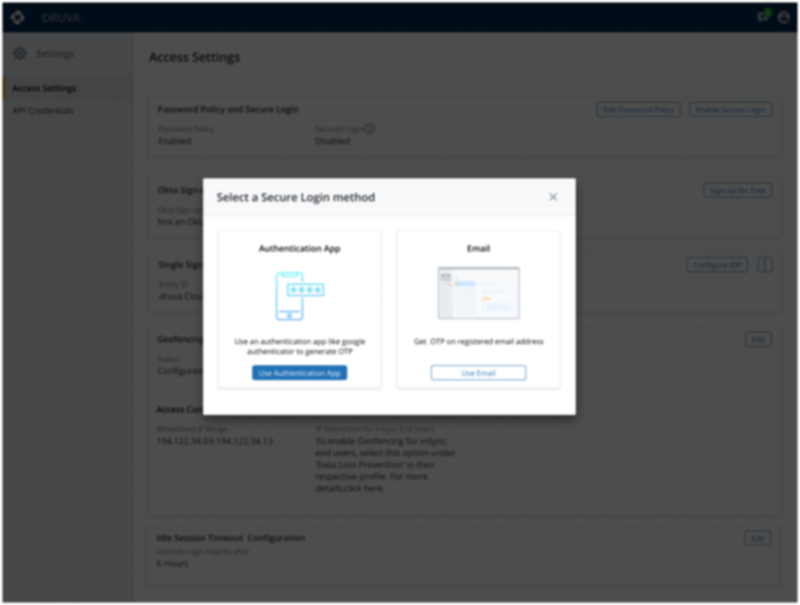
- Multi-Factor Authentication(Project 1) - To prevent Unauthorized access of DataInstead of using only Username and Password to access the Data we added one more layer of security as a form of OTP.
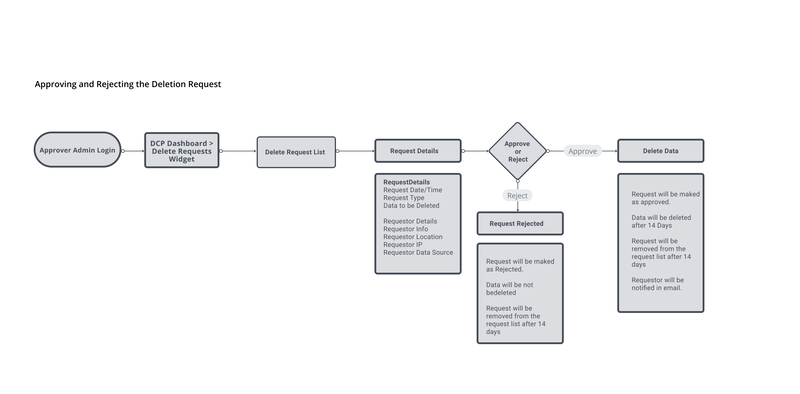
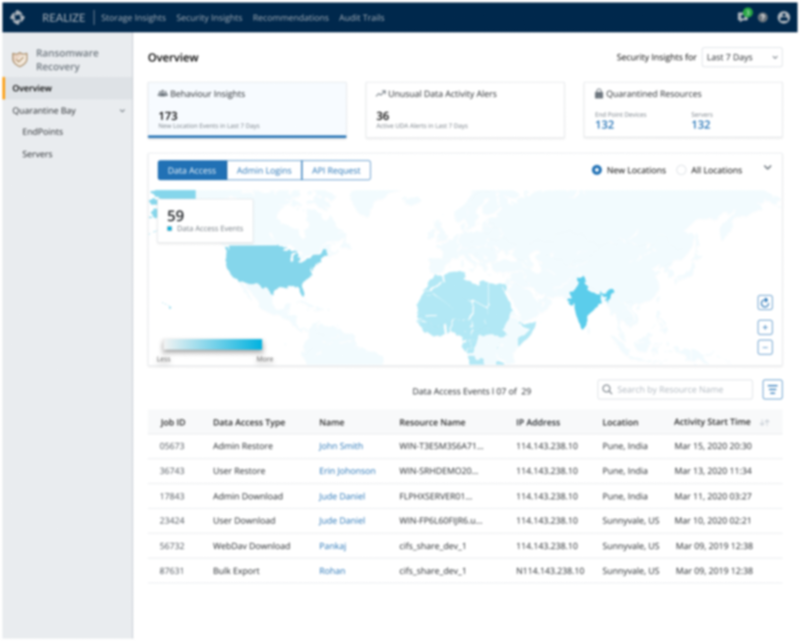
- Security Dashboard(Project 2) - To provide maximum visibility to security admins
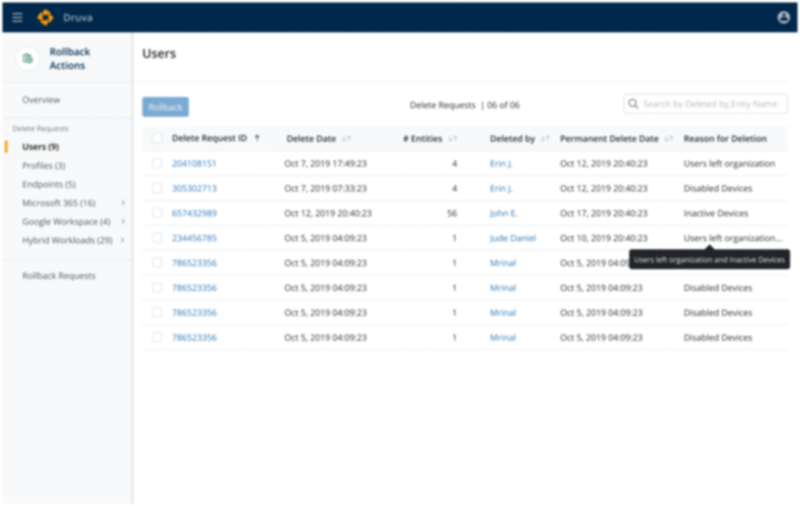
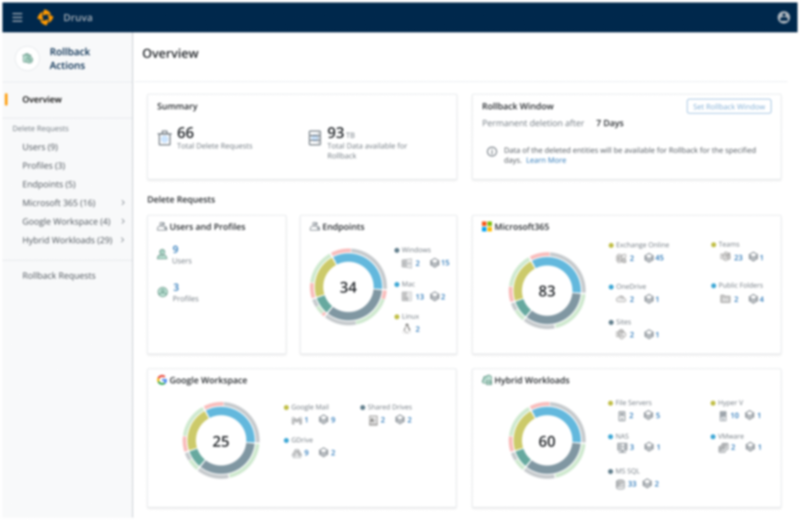
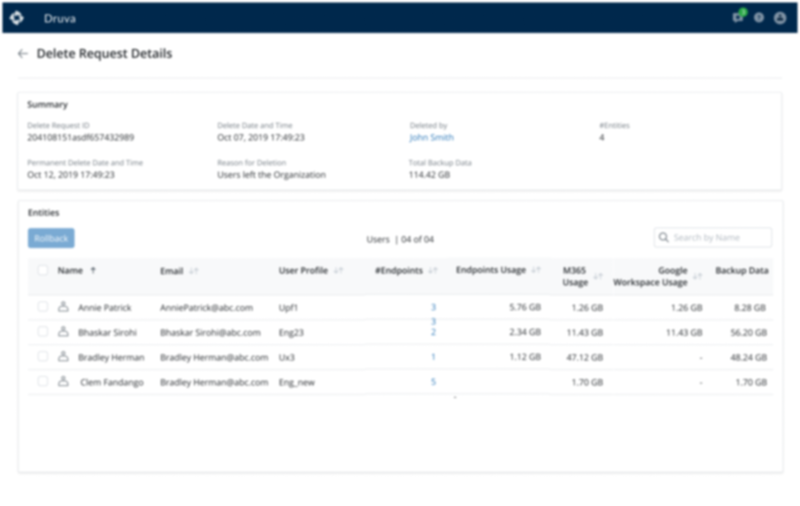
- Recycle Bin(Project 3) - To recover the accidentally deleted data or data deleted due to a security events
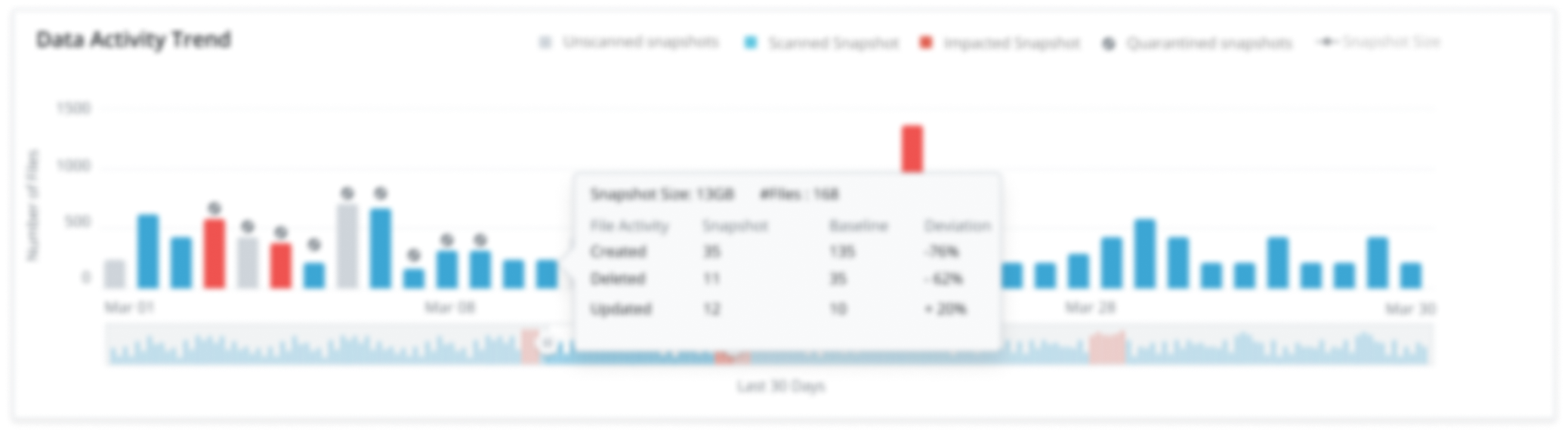
- Unusual Data Backup Analyzer(Project 4) - Analyzing the Customer data backup patterns through Artificial Intelligence
Design - Design Communication - Design Implementation - Usability Testing
|
|
Challenges and LearningsWorking with multiple teams and multiple stakeholders at the same time and acting as a bridge between Project Teams, Stakeholders and Users was one of the biggest challenge here. Live Project Links
(As it is a B2B Software Products. Adding the Product Documentation link here) Data Protection products for Data in Cloud Integrated Mass Deployment |